Crosssite request forgery (CSRF) vulnerability on Corega CGWLBARGMH and CGWLBARGNL devices allows remote attackers to hijack the authentication of administrators for requests that perform administrative functions not yet calculated CVE hpCrosssite request forgery (CSRF) vulnerability on Corega CGWLBARGMH and CGWLBARGNL devices allows remote attackers to hija HIGH CVE Corega CGWLNCM4G devices provide an open DNS resolver, which allows remote attackers to cause a denial of service (traffic a 58 MEDIUM CVECurrent Description Crosssite scripting vulnerability in Corega CGWLBARGMH and CGWLBARGNL allows remote attackers to inject arbitrary web script or

ルータ機能を無効化したい ブリッジモードにしたい Corepark
Cg-wlbargl-p
Cg-wlbargl-p-Is a list of records — each containing an identification number, a description, and at least one public reference — for publicly known cybersecurity vulnerabilities The mission of the CVE Program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilitiesCorega cgwlbargnl_firmware Crosssite scripting vulnerability in Corega CGWLBARGMH and CGWLBARGNL allows remote attackers to inject arbitrary web script or HTML via unspecified vectors 43 CVE CONFIRM(link is external) BID(link is external) JVN(link is external) corega cgwlr300nx_firmware




300 Nの値段と価格推移は 1 123件の売買情報を集計した300 Nの価格や価値の推移データを公開
OVAL, Open Vulnerability and Assessment Language, Definitions List of OVAL, Open Vulnerability and Assessment Language, definitionsPM 0400 V30 61 MEDIUM V 43 MEDIUM CVE1642コレガ社製「cgwlbargnlp」の設定例をご説明します。 他の設定方法やブロードバンドルーターの詳細 などについては、製品の取扱説明書をご覧ください。 不明な点については各メーカーのサポート窓口に お問い合わせください。 ※cgwlbargn, cgwlbargsx,
Korega CG Wlbargnl Draft IEEE N Normas Rutadores WLAN Amazoncommx Electrónicos Saltar al contenido principalcommx Hola Elige tu dirección Electrónicos Hola, Identifícate Cuenta y Listas Cuenta Devoluciones y Pedidos CarritoCorega CG Wlbargnl 2 Common Weakness Enumeration (CWE) CWE79 Improper Neutralization of Input During Web Page Generation ('Crosssite Scripting') Common Attack Pattern Enumeration and Classification (CAPEC) Cross Site Scripting through Log FilesCgwgr_10 cgwgr_10_firmware cgwlbaragm_firmware cgwlbargmh cgwlbargmh_firmware
Corega Cgwlbargnl security vulnerabilities, exploits, metasploit modules, vulnerability statistics and list of versions (eg CVE or or ) Log In Register## Description CGWLBARGL provided by Corega Inc is a wireless LAN router CGWLBARGL contains a command injection vulnerability ## Impact An arbitrary command may be executed by an authenticated attacker ## Solution Do not use CGWLBARGL As of Jun 22nd, 16, there are no practical solutions to this issue It is recommended to stop using CGWLBARGL無線セキュリティ設定を確認したい corePark 1ご利用の無線ルータのLANポート(1~4または1~3)のいずれかとパソコンをLAN ケーブルで接続します。 2「Internet Explorer」を開き、アドレス欄に「」を入力してエンターキー をクリックしてください




ヤフオク Cg 09年 08月号 ネットワーク の中古品 新品 未使用品一覧



2
CVE Crosssite scripting vulnerability in Corega CGWLBARGMH and CGWLBARGNL allows remote attackers to inject arbitrary web script or HTML via unspecified vectorsVendor Search Browse and select any vendor Vendor;Products List of Common Vulnerabilities and Exposures A basis for evaluation among tools and databases The way to interoperability and better security coverage




September 11 てんぐさんがころんだ




Corega Cg Wlbargnl 価格比較 価格 Com
Suscrito, y cuya información ha sido actualizada recientementeCrosssite scripting vulnerability in Corega CGWLBARGMH and CGWLBARGNL allows remote attackers to inject arbitrary web script or HTML via unspecified vectors Published ;Crosssite scripting vulnerability in Corega CGWLBARGMH and CGWLBARGNL allows remote attackers to inject arbitrary web script or HTML via unspecified vectors



無線ルーターの交換 法隆寺のm a




Audio Tv Home Theater Page Tv 3 Tv Tuner 5 Disc Allion
C rosssite request forgery (CSRF) vulnerability on Corega CGWLBARGMH and CGWLBARGNL devices allows remote attackers to hijack the authentication of administrators for requests that perform administrative functionsCWE CWE77 Improper Neutralization of Special Elements used in a Command ('Command Injection')Otras vulnerabilidades de los productos a los que usted está
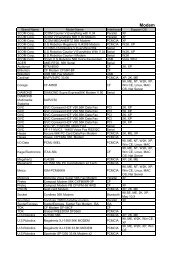



Audio Tv Home Theater Page Tv 3 Tv Tuner 5 Disc Allion




いつの間にかeo光1ギガコースに変更になって ルーターを変更したというお話 Sunabox
Corega cgwlbargnl_firmware Crosssite scripting vulnerability in Corega CGWLBARGMH and CGWLBARGNL allows remote attackers to inject arbitrary web script or HTML via unspecified vectors 43 CVE CONFIRM BID JVN corega cgwlr300nx_firmwareName CVE First vendor Publication Vendor Cve Last vendor ModificationCGWLBARGMH and CGWLBARGNL are no longer being supported, therefore fix for this vulnerability will not be provided Consider using the latest router, CG




Q608p4 無線lanルータ等 Wzr 900dhp2 Wlae Ag300n Wzr Hp Ag300h Bhr 4grv Whr G301n Wr8750n Wl300ne Ag Cg Wlbargnl Jauce Shopping Service Yahoo Japan Auctions Ebay Japan




ルータ機能を無効化したい ブリッジモードにしたい Corepark
CGWLBARGNL コレガは、IEEE n ドラフトに準拠した無線LAN製品「GNLシリーズ」を6月29日に発売する。 標準価格は無線LANルータ「CGWLBARGNL」が24,990円、無線LANカード「CGWLCB144GNL」が11,340円、USBアダプタ「CGWLUSB2GNL」が12,390円で、セットモデルも合わせて販売Corega CGWLBARGNL (donated by Kazuki Shimada) Airlink101 AR680W ixp4xx ADI Engineering Pronghorn SBC ALLNET ALL0276VPN DLink DWL7000AP Gateworks Avila GW234 Linksys RT042 Linksys WRV54G (donated by Kazuki Shimada) Planex BRCAP04 (donated by Kazuki Shimada) NTT RTI0KI (donated by Kazuki Shimada)Corega Cgwlbargnl Firmware security vulnerabilities, exploits, metasploit modules, vulnerability statistics and list of versions (eg CVE or or ) Log In Register




300 Nの値段と価格推移は 1 123件の売買情報を集計した300 Nの価格や価値の推移データを公開




Audio Tv Home Theater Page Tv 3 Tv Tuner 5 Disc Allion
As stewards of the lush and vast landscape of security vulnerabilities, we felt obliged to share with you the top trending CVEs of the past month (who's excited for winter to be over?!Details of vulnerability CVECrosssite scripting vulnerability in Corega CGWLBARGMH and CGWLBARGNL allows remote attackers to inject arbitrary web scriptログイン ようこそ、 ゲスト さん




メルカリ 無線lanルーター Corega Cg Wlbargnl Pc周辺機器 1 000 中古や未使用のフリマ




Your Partner Is Into Cg L Youtube
Cgwlbargnl cgwlbargnm cgwlbargns cgwlbargp cgwlbargpw cgwlbargpx cgwlbargpxbh cgwlbargs cgwlbargsx cgwlbargts cgwlr300gne cgwlr300gnh cgwlr300gnv cgwlr300gnz cgwlr300n cgwlr300nm cgwlr300nnh cgwlr300nx cgwlrgnxb elecom wmcc2533gst wmcm1267gst2w wmcx1800gst wrb300febk wrc1167febk2e wrc1167febkaオークファンntt nec他 ルーター モデムまとめ8台セット rt57i wrc300ghbk gepononu タイプd cgwlbargnl pr400ki pawd605cv padr2c aに入札した入札者の順位と入札額、最後に手動入札した時間を確認することができます。CVE Crosssite request forgery (CSRF) vulnerability on Corega CGWLBARGMH and CGWLBARGNL devices allows remote attackers to hijack the authentication of administrators for requests that perform administrative functions




ヨドバシ Com コレガ Corega 無線lan 通販 全品無料配達




ルータ機能を無効化したい ブリッジモードにしたい Corepark
Corega CGWLBARGNL (donated by Kazuki Shimada) Airlink101 AR680W ixp4xx ADI Engineering Pronghorn SBC ALLNET ALL0276VPN DLink DWL7000AP Gateworks Avila GW234 Linksys RT042 Linksys WRV54G (donated by Kazuki Shimada) Planex BRCAP04 (donated by Kazuki Shimada) NTT RTI0KI (donated by Kazuki Shimada) ppc40x Magicbox OpenRBCrosssite scripting vulnerability in Corega CGWLBARGMH and CGWLBARGNL allows remote attackers to inject arbitrary web script or HTML via unspecified vectors 75 CVE1643 Corega CGWLBARAGM devices allow remote attackers to cause a denial of service (reboot) via unspecified vectors 58 CVECGWLBARGNLP お気に入り登録 7 プッシュ通知が受け取れます 価格情報の登録がありません 価格推移グラフ お気に入り製品に登録すると、価格が掲載された時にメールやMyページでお知らせいたします 価格帯:¥―~¥― (―店舗) メーカー希望小売価格




Nuywceq3rgainm




楽天市場 コレガの通販
Description Crosssite request forgery (CSRF) vulnerability on Corega CGWLBARGMH and CGWLBARGNL devices allows remote attackers to hijack the authentication of administrators for requests that perform administrative functionsCVE CrossSite Request Forgery (CSRF) vulnerability in Corega CgWlbargmh Firmware and CgWlbargnl Firmware Crosssite request forgery (CSRF) vulnerability on Corega CGWLBARGMH and CGWLBARGNL devices allows remote attackers to hijack the authentication of administrators for requests that perform administrative functions## Description Multiple Corega wireless LAN routers contain a crosssite scripting vulnerability (CWE79) ## Impact An arbitrary script may be executed on the user's web browser ## Solution Use CGWLR300NX or CGWFR600 CGWLBARGMH and CGWLBARGNL are no longer being supported, therefore fix for this vulnerability will not be provided




無線セキュリティ設定を確認したい Corepark




ブロードバンドルーターの設定方法 コレガ社製cg Wlbargnl P ピカラお客さまサポート
Q608p4 無線lanルータ等 wzr900dhp2 wlaeag300n wzrhpag300h bhr4grv whrg301n wr8750n wl300neag cgwlbargnl 1,348Nuevas vulnerabilidades documentadas a los productos que usted estáCVE is a disclosure identifier tied to a security vulnerability with the following details Crosssite scripting vulnerability in Corega CGWLBARGMH and CGWLBARGNL allows remote attackers to inject arbitrary web script or HTML via unspecified vectors




Securenews コレガ製の無線lanルータ2機種に脆弱性 買い換える以外の対策はなし スラド



コレガ Cg Wlbarシリーズのルータ機能無効 ブリッジモード 設定 インターネット接続解説ブログkagemaru Info
An attacker manipulates inputs to the target software which the target software passes to file system calls in the OS The goal is to gain access to, and perhaps modify, areas of the file system that the target software did not intend to be accessible




特別企画 無線lanルータ比較リンク集 親機編




Lb N中2f スティールクロニクル筐体 ゲーム基板 ドングルなし Hdd内データ保証なし 日本代購代bid第一推介 Funbid




無線lan 三日坊主




September 11 てんぐさんがころんだ



高速無線lan情報局




価格 Com Cg Wlbargnl P の製品画像



Cg Wlrgnx コレガ の取扱説明書 マニュアル




Jvndb 16 Jvn Ipedia 脆弱性対策情報データベース




Cg Wlbargnの中古 未使用品を探そう メルカリ




Cg Wfr600 ファームウェア




B545m9 Audio Technica At Ma2 オーディオテクニカマイクロホンアンプ 日本代購代bid第一推介 Funbid




Ntt Nec他 ルーター モデムまとめ8台セット Rt57i Wrc 300ghbk Ge Pon Onu タイプd Cg Wlbargnl Pr 400ki Pa Wd605cv Pa Dr2c A の落札情報詳細 ヤフオク落札価格情報 オークフリー スマートフォン版




コレガ製の無線lanルータに複数の脆弱性 任意の操作を実行される可能性も Jvn Scannetsecurity



3 6 Nasをftpで公開する 読者の方より Lan 無線lan Wi Fi All About




Products Related Cve Cxsecurity Com




コレガ 無線lan Gnlシリーズ を40mhz通信に対応 新パッケージで発売 n R




Cg Wlbargnh マニュアル




Coregaの無線 Lan ルータに脆弱性 株式会社レオンテクノロジー




楽天市場 コレガの通販



Cg Wlbargnl コレガ の取扱説明書 マニュアル




メルカリ 無線lanルーター Corega Cg Wlbargnl Pc周辺機器 1 000 中古や未使用のフリマ



注意を呼びかけ コレガ製の無線lanルータに複数の脆弱性 リセマム



Wr9500nを買った のらり くらり ぶらり




ヨドバシ Com コレガ Corega Cg Wlbargnl Draft Ieee802 11n準拠 無線lanルータ 通販 全品無料配達




無線ルータと無線対応のプリンタを無線でつなぐことができますか Corepark
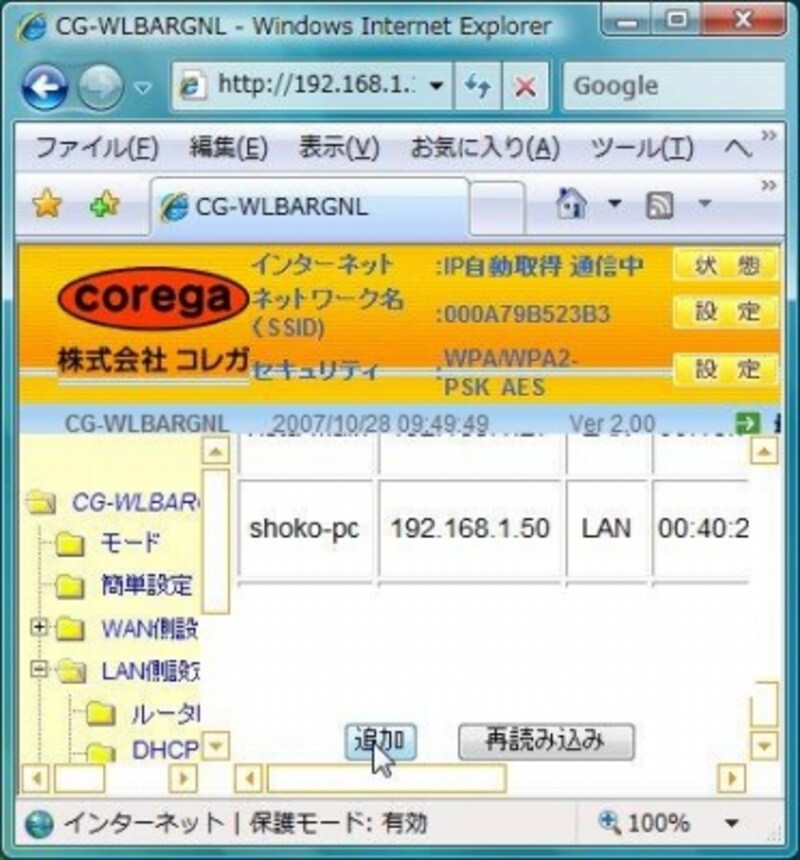



3 6 Nasをftpで公開する 読者の方より Lan 無線lan Wi Fi All About




Search Results For Wzr 900 Buyee Buyee Japanese Proxy Service Buy From Japan Bot Online
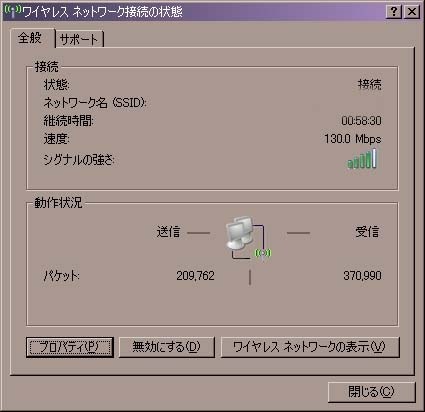



Corega Cg Wlbargnl U 価格比較 価格 Com
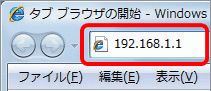



ブロードバンドルーターの設定方法 コレガ社製cg Wlbargnl P ピカラお客さまサポート



Photo




Cg Wlcvr300agn 取扱説明書 Manualzz




コレガ 無線lan規格ドラフトieee802 11nに準拠した無線lanルーターなど 3枚目の写真 画像 Rbb Today
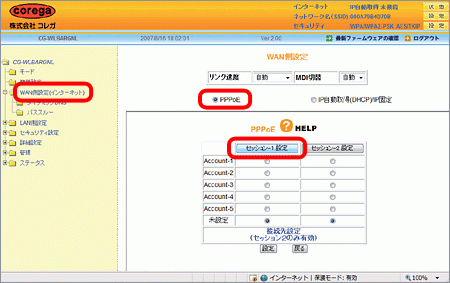



ブロードバンドルーターの設定方法 コレガ社製cg Wlbargnl P ピカラお客さまサポート




コレガ製の無線lanルータ2機種に脆弱性 買い換える以外の対策はなし 16年11月15日 エキサイトニュース




コレガ 無線lan規格ドラフトieee802 11nに準拠した無線lanルーターなど 2枚目の写真 画像 Rbb Today



高速無線lan情報局
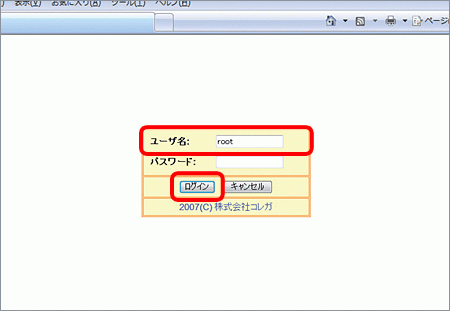



ブロードバンドルーターの設定方法 コレガ社製cg Wlbargnl P ピカラお客さまサポート




Ascii Jp コレガ Ieee 802 11n対応無線lanルーター5機種がリニューアル



Http Www Soumu Go Jp Soutsu Tohoku Houkoku H Shougyou Lan Pdf Shougyou Lan Pdf




メルカリ Corega 無線lanルータ Pc周辺機器 1 800 中古や未使用のフリマ



Cg Wlbargnl コレガ の取扱説明書 マニュアル



Http 153 127 246 254 Pdf 13 07 27 Pdf




Your Partner Is Into Cg L Youtube



Cg Wlbargnm コレガ の取扱説明書 マニュアル



Sheet001



Http Nice Kaze Com Cg Wlbargnh Man2 Pdf




Pcサポート 電脳系職人




Ascii Jp 07年6月26日のリリース
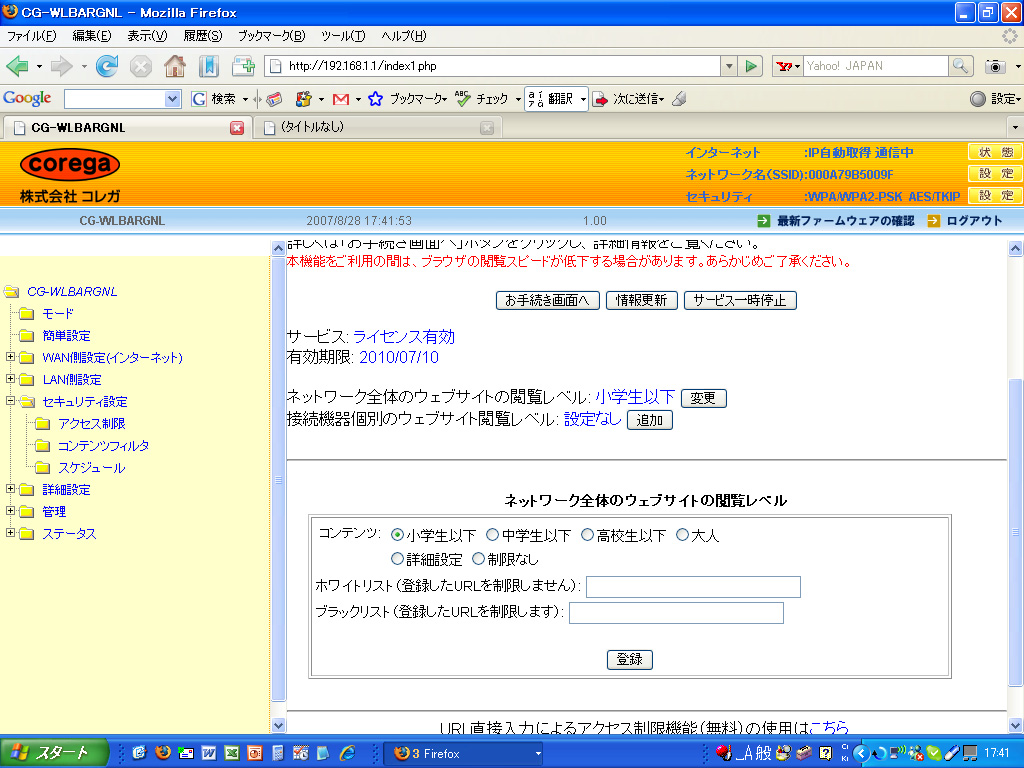



拡大画像




コレガ製無線lanルータ2機種に脆弱性 Ipaが注意喚起 マイナビニュース
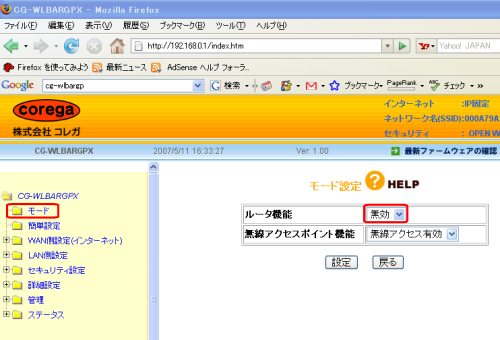



コレガ Cg Wlbarシリーズのルータ機能無効 ブリッジモード 設定 インターネット接続解説ブログkagemaru Info




Ntt Nec他 ルーター モデムまとめ8台セット Rt57i Wrc 300ghbk Ge Pon Onu タイプd Cg Wlbargnl Pr 400ki Pa Wd605cv Pa Dr2c A の落札情報詳細 ヤフオク落札価格情報 オークフリー スマートフォン版




ヤフオク Cg 09年 08月号 ネットワーク の中古品 新品 未使用品一覧




ヤフオク Wr8750 ネットワーク の中古品 新品 未使用品一覧




メルカリ 無線lanルーター Corega Cg Wlbargnl Pc周辺機器 1 000 中古や未使用のフリマ




インターネット Ps3を今まで使用していたルーターから新しいルーターに変 Okwave




コレガ Ieee802 11nドラフト準拠の無線lan Gnl シリーズ Rbb Today




Q608p4 無線lanルータ等 Wzr 900dhp2 Wlae Ag300n Wzr Hp Ag300h Bhr 4grv Whr G301n Wr8750n Wl300ne Ag Cg Wlbargnl Jauce Shopping Service Yahoo Japan Auctions Ebay Japan



コレガが直接 返品 返金 受け付けます コレガ




コレガ製の無線lanルータに複数の脆弱性 任意の操作を実行される可能性も Jvn 16年11月14日 エキサイトニュース



Http Nice Kaze Com Cg Wlbargnh Man2 Pdf




6 6 Nasをftpで公開する 読者の方より Lan 無線lan Wi Fi All About




Whr G301n おまかせ節電の値段と価格推移は 1件の売買情報を集計したwhr G301n おまかせ節電の価格や価値の推移データを公開



Http Nice Kaze Com Cg Wlbargnh Man2 Pdf




Cg Wlbarag2 マニュアル




Search Results For Corega 無線lan Buyee Buyee Japanese Proxy Service Buy From Japan Bot Online



2
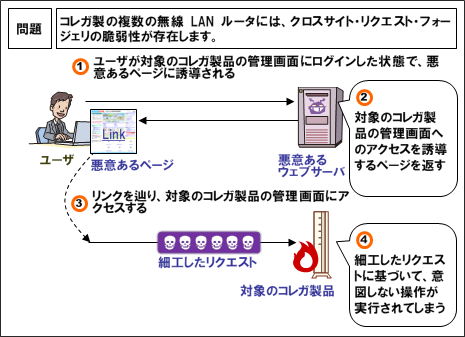



Jvndb 16 Jvn Ipedia 脆弱性対策情報データベース



家中どこでも快適接続 Corega製無線lan機器特集 自作pc Pcパーツが豊富 Pc専門店 Tsukumo




Q608p4 無線lanルータ等 Wzr 900dhp2 Wlae Ag300n Wzr Hp Ag300h Bhr 4grv Whr G301n Wr8750n Wl300ne Ag Cg Wlbargnl Jauce Shopping Service Yahoo Japan Auctions Ebay Japan



コレガが直接 返品 返金 受け付けます コレガ




Q608p4 無線lanルータ等 Wzr 900dhp2 Wlae Ag300n Wzr Hp Ag300h Bhr 4grv Whr G301n Wr8750n Wl300ne Ag Cg Wlbargnl Jauce Shopping Service Yahoo Japan Auctions Ebay Japan




特価blog919 08年09月



2




無線lanの延長機能について Planexのblw 54cw3という製品 Okwave




ブログas随筆or論文or外野の野次of妄想 12 08 12 09



Http 153 127 246 254 Pdf 13 07 27 Pdf




注意を呼びかけ コレガ製の無線lanルータに複数の脆弱性 リセマム


